Ad Blocker Detectado
Nuestro sitio web es posible al mostrar anuncios en línea a nuestros visitantes. Por favor considere apoyarnos deshabilitando su bloqueador de anuncios.
SUmario del cuestionario
0 de 52 preguntas completado
Preguntas:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
Información
CCNA 1 ITN New Questions 2016 Final Exam v5.03 + v5.1
Ya has realizado este cuestionario antes. Por tanto, no puedes empezarlo otra vez.
Cargando el cuestionario...
Debes ser un usuario registrado para poder realizar el cuestionario.
Tienes que terminar antes el siguiente cuestionario, para iniciar este cuestionario:
Resultados
0 de 52 preguntas contestadas correctamente
Tu tiempo:
El tiempo se ha terminado
Has conseguido 0 de 0 puntos posibles (0)
| Puntuación de promedio: |
|
| Tu puntuación |
|
Categorías
- No asignada a ninguna categoría 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- Contestada
- Revisada
-
Pregunta 1 de 52
1. Pregunta
-
Three bank employees are using the corporate network. The first employee uses a web browser to view a company web page in order to read some announcements. The second employee accesses the corporate database to perform some financial transactions. The third employee participates in an important live audio conference with other corporate managers in branch offices. If QoS is implemented on this network, what will be the priorities from highest to lowest of the different data types?
Correcto
Incorrecto
-
-
Pregunta 2 de 52
2. Pregunta
2. Refer to the exhibit. A network administrator is configuring access control to switch SW1. If the administrator has already logged into a Telnet session on the switch, which password is needed to access privileged EXEC mode?
 Correcto
Correcto
Incorrecto
-
Pregunta 3 de 52
3. Pregunta
3. What are the three primary functions provided by Layer 2 data encapsulation? (Choose three.)
Correcto
Incorrecto
-
Pregunta 4 de 52
4. Pregunta
4. What must be configured to enable Cisco Express Forwarding (CEF) on most Cisco devices that perform Layer 3 switching?
Correcto
Incorrecto
-
Pregunta 5 de 52
5. Pregunta
5. What is the purpose of adjacency tables as used in Cisco Express Forwarding (CEF)?
Correcto
Incorrecto
-
Pregunta 6 de 52
6. Pregunta
6. Which statement describes a characteristic of the network layer in the OSI model?
Correcto
Incorrecto
-
Pregunta 7 de 52
7. Pregunta
7. A user gets an IP address of 192.168.0.1 from the company network administrator. A friend of the user at a different company gets the same IP address on another PC. How can two PCs use the same IP address and still reach the Internet, send and receive email, and search the web?
Correcto
Incorrecto
-
Pregunta 8 de 52
8. Pregunta
8. At a minimum, which address is required on IPv6-enabled interfaces?
Correcto
Incorrecto
-
Pregunta 9 de 52
9. Pregunta
9. Why does HTTP use TCP as the transport layer protocol?
Correcto
Incorrecto
-
Pregunta 10 de 52
10. Pregunta
10. What is the binary representation of 0xCA?
Correcto
Incorrecto
-
Pregunta 11 de 52
11. Pregunta
11. What is the valid most compressed format possible of the IPv6 address 2001:0DB8:0000:AB00:0000:0000:0000:1234?
Correcto
Incorrecto
-
Pregunta 12 de 52
12. Pregunta
12. Refer to the exhibit. What is the maximum TTL value that is used to reach the destination http://www.cisco.com?
 Correcto
Correcto
Incorrecto
-
Pregunta 13 de 52
13. Pregunta
13. What field content is used by ICMPv6 to determine that a packet has expired?
Correcto
Incorrecto
-
Pregunta 14 de 52
14. Pregunta
14. Which statement is true about variable-length subnet masking?
Correcto
Incorrecto
-
Pregunta 15 de 52
15. Pregunta
15. Which firewall technique blocks incoming packets unless they are responses to internal requests?
Correcto
Incorrecto
-
Pregunta 16 de 52
16. Pregunta
16. A network technician is investigating network connectivity from a PC to a remote host with the address 10.1.1.5. Which command issued on the PC will return to the technician the complete path to the remote host?
Correcto
Incorrecto
-
Pregunta 17 de 52
17. Pregunta
17. Fill in the blank.
- To prevent faulty network devices from carrying dangerous voltage levels, equipment must be (grounded, Grounded) correctly
Correcto
Incorrecto
-
Pregunta 18 de 52
18. Pregunta
18. A network engineer is measuring the transfer of bits across the company backbone for a mission critical database application. The engineer notices that the network throughput appears lower than the bandwidth expected. Which three factors could influence the differences in throughput? (Choose three.)
Correcto
Incorrecto
-
Pregunta 19 de 52
19. Pregunta
19. What is a possible hazard that can be caused by network cables in a fire?
Correcto
Incorrecto
-
Pregunta 20 de 52
20. Pregunta
20. What device is commonly used to verify a UTP cable?
Correcto
Incorrecto
-
Pregunta 21 de 52
21. Pregunta
21. What needs to be checked when testing a UTP network cable?
Correcto
Incorrecto
-
Pregunta 22 de 52
22. Pregunta
22. Refer to the exhibit. A ping to PC2 is issued from PC0, PC1, and PC3 in this exact order. Which MAC addresses will be contained in the S1 MAC address table that is associated with the Fa0/1 port?
 Correcto
Correcto
Incorrecto
-
Pregunta 23 de 52
23. Pregunta
23. Which function is provided by TCP?
Correcto
Incorrecto
-
Pregunta 24 de 52
24. Pregunta
24. What does a router use to determine where to send data it receives from the network?
Correcto
Incorrecto
-
Pregunta 25 de 52
25. Pregunta
25. Which router interface should be used for direct remote access to the router via a modem?
Correcto
Incorrecto
-
Pregunta 26 de 52
26. Pregunta
26. A technician is configuring a router to allow for all forms of management access. As part of each different type of access, the technician is trying to type the command login. Which configuration mode should be entered to do this task?
Correcto
Incorrecto
-
Pregunta 27 de 52
27. Pregunta
27. Which three statements characterize the transport layer protocols? (Choose three.)
Correcto
Incorrecto
-
Pregunta 28 de 52
28. Pregunta
28. Refer to the exhibit. A TCP segment from a server has been captured by Wireshark, which is running on a host. What acknowledgement number will the host return for the TCP segment that has been received?
 Correcto
Correcto
Incorrecto
-
Pregunta 29 de 52
29. Pregunta
29. Which statement is true about an interface that is configured with the IPv6 address command?
Correcto
Incorrecto
-
Pregunta 30 de 52
30. Pregunta
30. Refer to the exhibit. The network administrator for a small advertising company has chosen to use the 192.168.5.96/27 network for internal LAN addressing. As shown in the exhibit, a static IP address is assigned to the company web server. However, the web server cannot access the Internet. The administrator verifies that local workstations with IP addresses that are assigned by a DHCP server can access the Internet, and the web server is able to ping local workstations. Which component is incorrectly configured?
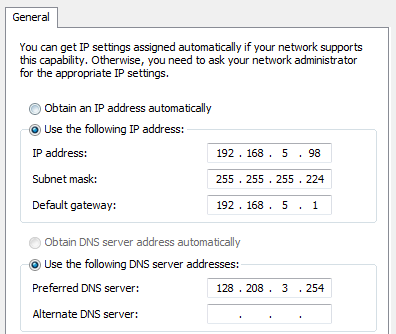 Correcto
Correcto
Incorrecto
-
Pregunta 31 de 52
31. Pregunta
31. Refer to the exhibit. An administrator must send a message to everyone on the router A network. What is the broadcast address for network 172.16.16.0/22?
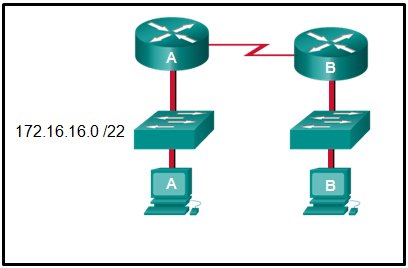 Correcto
Correcto
Incorrecto
-
Pregunta 32 de 52
32. Pregunta
32. A network administrator is variably subnetting a given block of IPv4 addresses. Which combination of network addresses and prefix lengths will make the most efficient use of addresses when the need is for 2 subnets capable of supporting 10 hosts and 1 subnet that can support 6 hosts?
Correcto
Incorrecto
-
Pregunta 33 de 52
33. Pregunta
33. How many additional bits should be borrowed from a /26 subnet mask in order to create subnets for WAN links that need only 2 useable addresses?
Correcto
Incorrecto
-
Pregunta 34 de 52
34. Pregunta
34. Fill in the blank.
- A (logical, LOGICAL) topology influences the type of network framing and media access control that will be used.
Correcto
Incorrecto
-
Pregunta 35 de 52
35. Pregunta
35. Refer to the exhibit. The administrator configured the access to the console and the vty lines of a router. Which conclusion can be drawn from this configuration?
 Correcto
Correcto
Incorrecto
-
Pregunta 36 de 52
36. Pregunta
36. An administrator issued the service password-encryption command to apply encryption to the passwords configured for enable password, vty, and console lines. What will be the consequences if the administrator later issues the no service password-encryption command?
Correcto
Incorrecto
-
Pregunta 37 de 52
37. Pregunta
37. After making configuration changes, a network administrator issues a copy running-config startup-config command in a Cisco switch. What is the result of issuing this command?
Correcto
Incorrecto
-
Pregunta 38 de 52
38. Pregunta
38. What are two features of ARP? (Choose two.)
Correcto
Incorrecto
-
Pregunta 39 de 52
39. Pregunta
39. What are two examples of the cut-through switching method? (Choose two.)
Correcto
Incorrecto
-
Pregunta 40 de 52
40. Pregunta
40. A network administrator is enabling services on a newly installed server. Which two statements describe how services are used on a server? (Choose two.)
Correcto
Incorrecto
-
Pregunta 41 de 52
41. Pregunta
41. Why does a Layer 3 device perform the ANDing process on a destination IP address and subnet mask?
Correcto
Incorrecto
-
Pregunta 42 de 52
42. Pregunta
42. Given the binary address of 11101100 00010001 00001100 00001010, which address does this represent in dotted decimal format?
Correcto
Incorrecto
-
Pregunta 43 de 52
43. Pregunta
43. A particular telnet site does not appear to be responding on a Windows 7 computer. What command could the technician use to show any cached DNS entries for this web page?
Correcto
Incorrecto
-
Pregunta 44 de 52
44. Pregunta
44. Fill in the blank.
- Network devices come in two physical configurations. Devices that have expansion slots that provide the flexibility to add new modules have a (Modular, modular) configuration.
Correcto
Incorrecto
-
Pregunta 45 de 52
45. Pregunta
45.

Refer to the exhibit. What is the maximum TIL value that is used to reach the destination http://www.cisco.com?Correcto
Incorrecto
-
Pregunta 46 de 52
46. Pregunta
46. Which statement is true about DHCP operation?
Correcto
Incorrecto
-
Pregunta 47 de 52
47. Pregunta
47. Which type of wireless security is easily compromised?
Correcto
Incorrecto
-
Pregunta 48 de 52
48. Pregunta
48. A network administrator notices that the throughput on the network appears lower than expected when compared to the end-to-end network bandwidth. Which three factors can
explain this difference? (Choose three.)Correcto
Incorrecto
-
Pregunta 49 de 52
49. Pregunta
49. A host PC is attempting to lease an address through DHCP. What message is sent by the server to the client know it is able to use the provided IP information?
Correcto
Incorrecto
-
Pregunta 50 de 52
50. Pregunta
50. A network administrator is configuring access control to switch SW1. If the administrator uses console line to connect to the switch, which password is needed to access user EXEC mode?
 Correcto
Correcto
Incorrecto
-
Pregunta 51 de 52
51. Pregunta
51. What is a characteristic of UTP cabling?
Correcto
Incorrecto
-
Pregunta 52 de 52
52. Pregunta
52. How many bits would need to be borrowed if a network admin were given the IP addressing scheme of 172.16.0.0/16 and needed no more than 16 subnet with equal number of hosts?
Correcto
Incorrecto
