Ad Blocker Detectado
Nuestro sitio web es posible al mostrar anuncios en línea a nuestros visitantes. Por favor considere apoyarnos deshabilitando su bloqueador de anuncios.
SUmario del cuestionario
0 de 29 preguntas completado
Preguntas:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
Información
CCNA 3 Chapter 4 v5 Exam Answers
Ya has realizado este cuestionario antes. Por tanto, no puedes empezarlo otra vez.
Cargando el cuestionario...
Debes ser un usuario registrado para poder realizar el cuestionario.
Tienes que terminar antes el siguiente cuestionario, para iniciar este cuestionario:
Resultados
0 de 29 preguntas contestadas correctamente
Tu tiempo:
El tiempo se ha terminado
Has conseguido 0 de 0 puntos posibles (0)
| Puntuación de promedio: |
|
| Tu puntuación |
|
Categorías
- No asignada a ninguna categoría 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- Contestada
- Revisada
-
Pregunta 1 de 29
1. Pregunta
1.

Launch PT Hide and Save PT
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
What is the SSID of the connected network and which message is displayed in the browser window?Correcto
Incorrecto
-
Pregunta 2 de 29
2. Pregunta
2.
A administrator wishes to extend the range of the existing IEEE 802.11n network without changing the AP. What can the administrator do to accomplish this?Correcto
Incorrecto
-
Pregunta 3 de 29
3. Pregunta
3. Which security mode is the least secure choice when a home wireless router is configured?
Correcto
Incorrecto
-
Pregunta 4 de 29
4. Pregunta
4. Which two roles are typically performed by a wireless router that is used in a home or small business? (Choose two.)
Correcto
Incorrecto
-
Pregunta 5 de 29
5. Pregunta
5. Which organization certifies vendors for adherence to the 802.11 standards to improve interoperability of 802.11 products?
Correcto
Incorrecto
-
Pregunta 6 de 29
6. Pregunta
6. Which feature of 802.11n wireless access points allows them to transmit data at faster speeds than previous versions of 802.11 Wi-Fi standards did?
Correcto
Incorrecto
-
Pregunta 7 de 29
7. Pregunta
7. Which type of wireless topology is created when two or more Basic Service Sets are interconnected by Ethernet?
Correcto
Incorrecto
-
Pregunta 8 de 29
8. Pregunta
8. If three 802.11b access points need to be deployed in close proximity, which three frequency channels should be used? (Choose three.)
Correcto
Incorrecto
-
Pregunta 9 de 29
9. Pregunta
9. What type of wireless antenna is best suited for providing coverage in large open spaces, such as hallways or large conference rooms?
Correcto
Incorrecto
-
Pregunta 10 de 29
10. Pregunta
10. Which three Wi-Fi standards operate in the 2.4GHz range of frequencies? (Choose three.)
Correcto
Incorrecto
-
Pregunta 11 de 29
11. Pregunta
11. What is the purpose of the Distributed Coordination Function in an IEEE 802.11 WLAN environment?
Correcto
Incorrecto
-
Pregunta 12 de 29
12. Pregunta
12. An employee connects wirelessly to the company network using a cell phone. The employee then configures the cell phone to act as a wireless access point that will allow new employees to connect to the company network. Which type of security threat best describes this situation?
Correcto
Incorrecto
-
Pregunta 13 de 29
13. Pregunta
13. During which stage of establishing connectivity between a WLAN client and an AP does the client learn the MAC address of the AP?
Correcto
Incorrecto
-
Pregunta 14 de 29
14. Pregunta
14. Fill in the blank. Do not use abbreviations.
- Ad hoc wireless topologies sometimes can use a feature called (tethering, TETHERING) to enable a smartphone to create a personal hotspot.
Correcto
Incorrecto
-
Pregunta 15 de 29
15. Pregunta
15. What is an advantage of SSID cloaking?
Correcto
Incorrecto
-
Pregunta 16 de 29
16. Pregunta
16. A student uses a laptop to upload an assignment to a file server. Which wireless frame type did the laptop send to locate and associate with the campus access point?
Correcto
Incorrecto
-
Pregunta 17 de 29
17. Pregunta
17. Which type of management frame may regularly be broadcast by an AP?
Correcto
Incorrecto
-
Pregunta 18 de 29
18. Pregunta
18. A company has recently implemented an 802.11n wireless network. Some users are complaining that the wireless network is too slow. Which solution is the best method to enhance the performance of the wireless network?
Correcto
Incorrecto
-
Pregunta 19 de 29
19. Pregunta
19. For which discovery mode will an AP generate the most traffic on a WLAN?
Correcto
Incorrecto
-
Pregunta 20 de 29
20. Pregunta
20. Which statement defines the control frame operation between two stations?
Correcto
Incorrecto
-
Pregunta 21 de 29
21. Pregunta
21. What is a difference between Cisco APs that operate in a home environment and Cisco APs that operate in a corporate environment?
Correcto
Incorrecto
-
Pregunta 22 de 29
22. Pregunta
22. Match the type of attack to its description. (Not all options are used.)
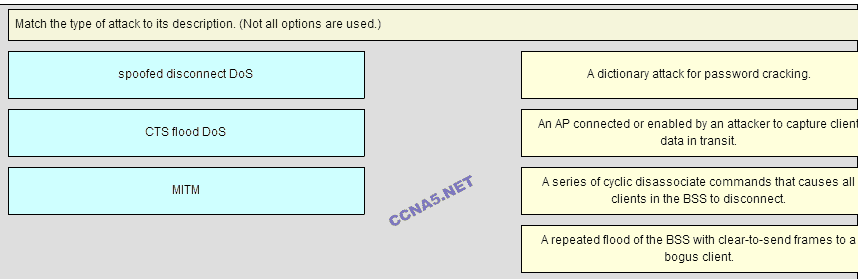
Ordenar elementos
- AN AP connected or enabled by an attacker to capture client data in transit.
- A series of cyclic dissasociate commands that causes all clients in the BSS to disconnect.
- A repeated flood of the BSS with clear-to-send frames to a bogus client.
-
MITM
-
spoofed disconnct DoS
-
CTS flood DoS
Correcto
Incorrecto
-
Pregunta 23 de 29
23. Pregunta
23. Place the following actions in the order in which they occur in a shared key authentication process. (Not all options are used.)

Ordenar elementos
- The AP send a challenge text to the client.
- The AP authenticates the client.
- The client sends an authentication frame to the AP.
- The client encrypts the message.
- The AP decypts the message.
-
Step 2
-
Step 5
-
Step 1
-
Step 3
-
Step 4
Correcto
Incorrecto
-
Pregunta 24 de 29
24. Pregunta
24. Fill in the blank. Use the acronym.
- Which encryption protocol is used by the WPA2 shared key authentication technique? (AES)
Correcto
Incorrecto
-
Pregunta 25 de 29
25. Pregunta
25. A WLAN user wants to allocate an optimal amount of bandwidth to a specific online game. What is a Linksys Smart Wi-Fi tool that will allow the user to do this?
Correcto
Incorrecto
-
Pregunta 26 de 29
26. Pregunta
26. Which parameter is commonly used to identify a wireless network name when a home wireless AP is being configured?
Correcto
Incorrecto
-
Pregunta 27 de 29
27. Pregunta
27. A supervisor needs wireless access in the construction office during the construction of a new building. The construction office is in the new building and directly across the road from headquarters. What could be used to satisfy this requirement of needing a narrow area of coverage?
Correcto
Incorrecto
-
Pregunta 28 de 29
28. Pregunta
28. Which IEEE wireless standard is known as WiGig and operates using a tri-band solution in the 2.4, 5, and 60 GHz ranges?
Correcto
Incorrecto
-
Pregunta 29 de 29
29. Pregunta
29. Fill in the blank.
- A network administrator discovers a rogue AP in the network. The rogue AP is capturing traffic and then forwarding it on to the legitimate AP. This type of attack is known as a (man in the middle, MAN IN THE MIDDLE)attack.
Correcto
Incorrecto
