Ad Blocker Detectado
Nuestro sitio web es posible al mostrar anuncios en línea a nuestros visitantes. Por favor considere apoyarnos deshabilitando su bloqueador de anuncios.
SUmario del cuestionario
0 de 30 preguntas completado
Preguntas:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
Información
CCNA 4 Chapter 7 v5 Exam Answers
Ya has realizado este cuestionario antes. Por tanto, no puedes empezarlo otra vez.
Cargando el cuestionario...
Debes ser un usuario registrado para poder realizar el cuestionario.
Tienes que terminar antes el siguiente cuestionario, para iniciar este cuestionario:
Resultados
0 de 30 preguntas contestadas correctamente
Tu tiempo:
El tiempo se ha terminado
Has conseguido 0 de 0 puntos posibles (0)
| Puntuación de promedio: |
|
| Tu puntuación |
|
Categorías
- No asignada a ninguna categoría 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- Contestada
- Revisada
-
Pregunta 1 de 30
1. Pregunta
1. How is “tunneling” accomplished in a VPN?
Correcto
Incorrecto
-
Pregunta 2 de 30
2. Pregunta
2. Which two scenarios are examples of remote access VPNs? (Choose two.)
Correcto
Incorrecto
-
Pregunta 3 de 30
3. Pregunta
3.

Refer to the exhibit. Which IP address would be configured on the tunnel interface of the destination router?Correcto
Incorrecto
-
Pregunta 4 de 30
4. Pregunta
4. Which statement correctly describes IPsec?
Correcto
Incorrecto
-
Pregunta 5 de 30
5. Pregunta
5. What is an IPsec protocol that provides data confidentiality and authentication for IP packets?
Correcto
Incorrecto
-
Pregunta 6 de 30
6. Pregunta
6. Which three statements describe the building blocks that make up the IPsec protocol framework? (Choose three.)
Correcto
Incorrecto
-
Pregunta 7 de 30
7. Pregunta
7. What key question would help determine whether an organization should use an SSL VPN or an IPsec VPN for the remote access solution of the organization?
Correcto
Incorrecto
-
Pregunta 8 de 30
8. Pregunta
8. What is the purpose of a message hash in a VPN connection?
Correcto
Incorrecto
-
Pregunta 9 de 30
9. Pregunta
9. A network design engineer is planning the implementation of a cost-effective method to interconnect multiple networks securely over the Internet. Which type of technology is required?
Correcto
Incorrecto
-
Pregunta 10 de 30
10. Pregunta
10. What is one benefit of using VPNs for remote access?
Correcto
Incorrecto
-
Pregunta 11 de 30
11. Pregunta
11. Which statement describes a characteristic of IPsec VPNs?
Correcto
Incorrecto
-
Pregunta 12 de 30
12. Pregunta
12. What is the purpose of the generic routing encapsulation tunneling protocol?
Correcto
Incorrecto
-
Pregunta 13 de 30
13. Pregunta
13. Which algorithm is an asymmetrical key cryptosystem?
Correcto
Incorrecto
-
Pregunta 14 de 30
14. Pregunta
14. A network design engineer is planning the implementation of an IPsec VPN. Which hashing algorithm would provide the strongest level of message integrity?
Correcto
Incorrecto
-
Pregunta 15 de 30
15. Pregunta
15. What two encryption algorithms are used in IPsec VPNs? (Choose two.)
Correcto
Incorrecto
-
Pregunta 16 de 30
16. Pregunta
16. Which statement describes a feature of site-to-site VPNs?
Correcto
Incorrecto
-
Pregunta 17 de 30
17. Pregunta
17. Which Cisco VPN solution provides limited access to internal network resources by utilizing a Cisco ASA and provides browser-based access only?
Correcto
Incorrecto
-
Pregunta 18 de 30
18. Pregunta
18. Which two algorithms use Hash-based Message Authentication Code for message authentication? (Choose two.)
Correcto
Incorrecto
-
Pregunta 19 de 30
19. Pregunta
19. Which function of IPsec security services allows the receiver to verify that the data was transmitted without being changed or altered in any way?
Correcto
Incorrecto
-
Pregunta 20 de 30
20. Pregunta
20.
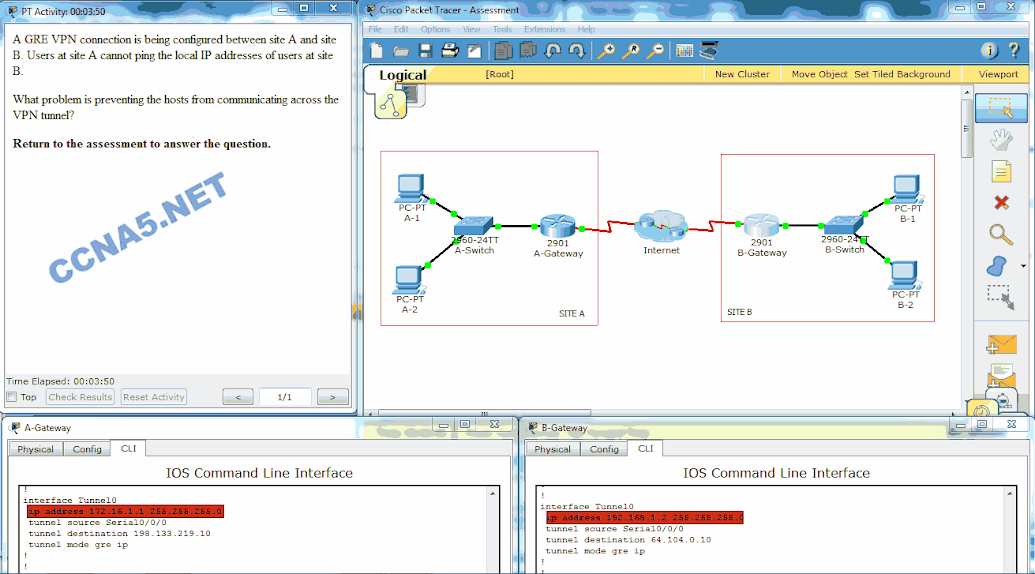
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. What problem is preventing the hosts from communicating across the VPN tunnel?
Correcto
Incorrecto
-
Pregunta 21 de 30
21. Pregunta
21. What is the purpose of utilizing Diffie-Hellman (DH) algorithms as part of the IPsec standard?
Correcto
Incorrecto
-
Pregunta 22 de 30
22. Pregunta
22.

Refer to the exhibit. A tunnel was implemented between routers R1 and R2. Which two conclusions can be drawn from the R1 command output? (Choose two.)
Correcto
Incorrecto
-
Pregunta 23 de 30
23. Pregunta
23. Two corporations have just completed a merger. The network engineer has been asked to connect the two corporate networks without the expense of leased lines. Which solution would be the most cost effective method of providing a proper and secure connection between the two corporate networks?
Correcto
Incorrecto
-
Pregunta 24 de 30
24. Pregunta
24. Which remote access implementation scenario will support the use of generic routing encapsulation tunneling?
Correcto
Incorrecto
-
Pregunta 25 de 30
25. Pregunta
25. Which critical function that is provided by IPsec ensures that data has not been changed in transit between the source and destination?
Correcto
Incorrecto
-
Pregunta 26 de 30
26. Pregunta
26. Which service of IPsec verifies that secure connections are formed with the intended sources of data?
Correcto
Incorrecto
-
Pregunta 27 de 30
27. Pregunta
27. Fill in the blank.
- (GRE) is a site-to-site tunnel protocol developed by Cisco to allow multiprotocol and IP multicast traffic between two or more sites.
Correcto
Incorrecto
-
Pregunta 28 de 30
28. Pregunta
28. What is an advantage of using the Cisco Secure Mobility Clientless SSL VPN?
Correcto
Incorrecto
-
Pregunta 29 de 30
29. Pregunta
29. How can the use of VPNs in the workplace contribute to lower operating costs?
Correcto
Incorrecto
-
Pregunta 30 de 30
30. Pregunta
30. Which two characteristics describe IPsec VPNs? (Choose two.)
Correcto
Incorrecto
